Active Reconnaissance:
Active Reconnaissance is a crucial phase in cybersecurity where attackers actively probe and gather information about a target system or network. Here are the key steps, organized in a short list with subpoints:
Footprinting:
Determine the target's IP addresses.
Discover domain names and subdomains.
Identify network topology.
Scanning:
Port scanning to find open ports.
OS fingerprinting to determine the target's operating system.
Service enumeration to identify running services and versions.
Enumeration:
Gather information about users and groups.
Extract system and network configuration details.
Enumerate shares, printers, and resources.
Vulnerability Scanning:
Use automated tools to identify known vulnerabilities.
Assess the target's susceptibility to specific exploits.
Brute-Force Attacks:
Attempt username/password combinations.
Use dictionary attacks and password guessing.
Social Engineering:
Phishing to manipulate individuals for information.
Deceptive tactics to trick employees into revealing sensitive data.
Exploitation:
Exploit discovered vulnerabilities to gain unauthorized access.
Deploy malware or malicious scripts.
Active Reconnaissance is often used by both ethical hackers (penetration testers) to improve security and malicious actors for malicious purposes. Organizations need to defend against these tactics through robust security measures, including firewalls, intrusion detection systems, and employee training.
Web Browser
The web browser can be a convenient tool, especially that it is readily available on all systems. There are several ways where you can use a web browser to gather information about a target.
On the transport level, the browser connects to:
TCP port 80 by default when the website is accessed over HTTP
TCP port 443 by default when the website is accessed over HTTPS
Here's the information rearranged for clarity:
Browser Add-ons for Penetration Testing:
FoxyProxy:
Allows quick proxy server switching.
Handy for tools like Burp Suite.
Useful for switching proxy servers.
User-Agent Switcher and Manager:
Enables impersonation of different OS or browsers.
Example: Appear as if browsing from an iPhone using Mozilla Firefox.
Wappalyzer:
Provides insights into technologies used on visited websites.
Useful for gathering information like a regular user.
These browser add-ons are valuable for penetration testers and security professionals to enhance their reconnaissance and testing capabilities.
Q : Browse to the following website and ensure that you have opened your Developer Tools on AttackBox Firefox, or the browser on your computer. Using the Developer Tools, figure out the total number of questions.
~ 8
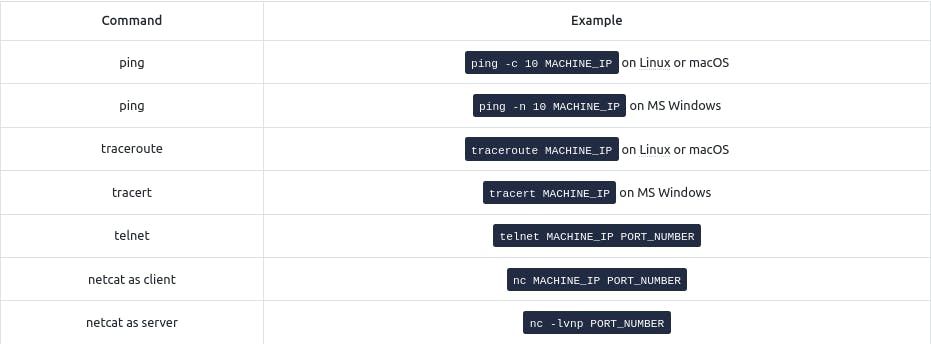
Ping
Concept: Think of ping like a game of ping-pong. You hit the ball and expect it to come back. Similarly, ping checks if you can reach a remote system and if it can reach you.
Purpose: Initially used for network connectivity, now mainly used to see if a remote system is online.
How it Works: Ping sends a packet to a remote system, and if it's online, the system replies. This confirms both the system's online status and network connectivity.
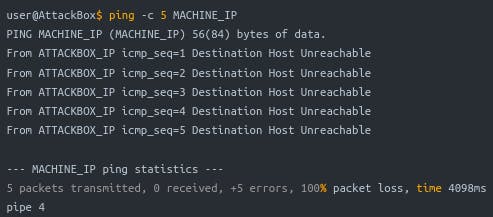
Technical Details: Ping uses ICMP (Internet Control Message Protocol) to send an "echo" packet. If the remote system is online and not blocked by firewalls, it sends an "echo reply."
Why It Matters: Helps confirm the target system's online status before performing more detailed scans for operating systems and services.
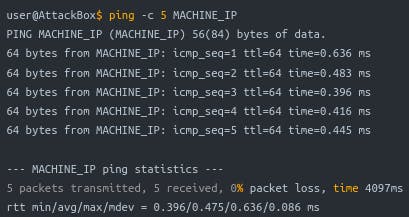
Usage: On the AttackBox terminal, use "ping MACHINE_IP" or "ping HOSTNAME" (which resolves to an IP). Add "-c 10" to send ten packets (Linux) or "-n 10" (Windows) to limit the count.
ICMP: Ping uses ICMP, specifically ICMP echo (type 8) and echo reply (type 0). Understanding ICMP details isn't necessary for using ping.
Example: If you ping a system with a count of 5 packets, you'll know if it's up and not blocking ICMP echo requests. Firewalls and routers along the route shouldn't block them either.
Q : Which option would you use to set the size of the data carried by the ICMP echo request?
~ -s
Q : What is the size of the ICMP header in bytes?
~ 8
Q : Does MS Windows Firewall block ping by default? (Y/N)
~ y
Q : Deploy the VM for this task and using the AttackBox terminal, issue the command ping -c 10 MACHINE_IP. How many ping replies did you get back?
~ 10
Traceroute
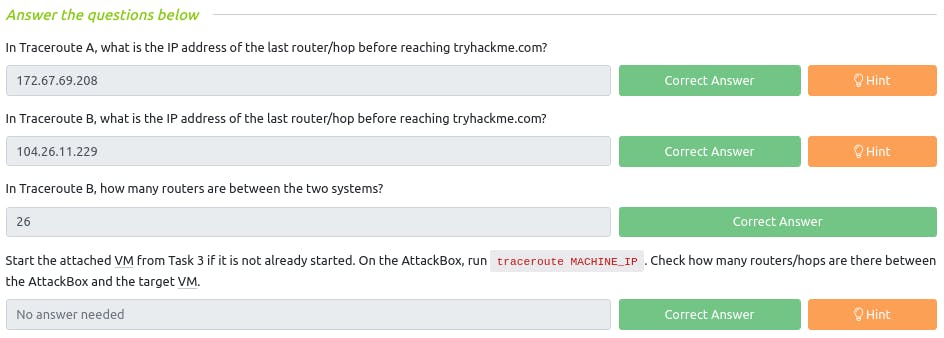
Q : In Traceroute A, what is the IP address of the last router/hop before reaching tryhackme.com?
~ 172.67.69.208
Q : In Traceroute B, what is the IP address of the last router/hop before reaching tryhackme.com?
~ 104.26.11.229
Q : In Traceroute B, how many routers are between the two systems?
~ 26
Telnet
TELNET Protocol and Its Insecurity:
TELNET (Teletype Network) protocol created in 1969 for remote system communication via command-line interface (CLI).
Command telnet uses TELNET for remote administration, default port is 23.
Security concern: Telnet sends all data, including usernames and passwords, in cleartext, easily accessible to anyone on the communication channel.
Secure alternative: SSH (Secure SHell) protocol.
Other Uses of Telnet Client:
Telnet client can serve other purposes due to simplicity and reliance on TCP protocol.
Connecting to any service: Use Telnet to connect to any service and retrieve its banner.
For example, to discover info about a web server on port 80, connect to it and communicate using HTTP protocol.
Issue GET / HTTP/1.1 to request the default index page.
To specify a different page, use GET /page.html HTTP/1.1.
Specify HTTP version with HTTP/1.1.
To receive a valid response, provide a value for the host with host: example and hit enter twice.
Follow these steps to obtain the requested index page
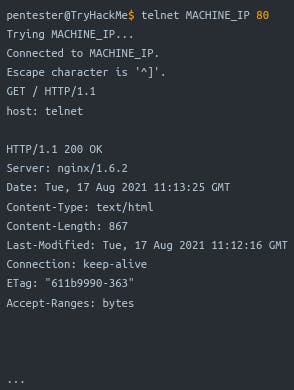
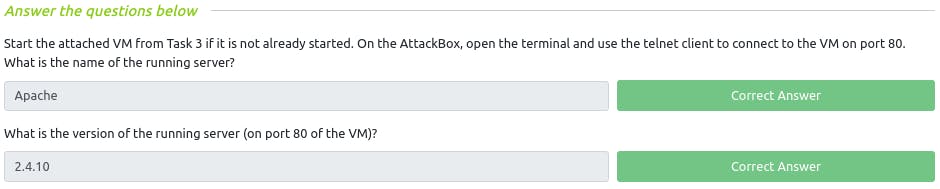
Q : Start the attached VM from Task 3 if it is not already started. On the AttackBox, open the terminal and use the telnet client to connect to the VM on port 80. What is the name of the running server?
~
ApacheQ : What is the version of the running server (on port 80 of the VM)?
~
2.4.10
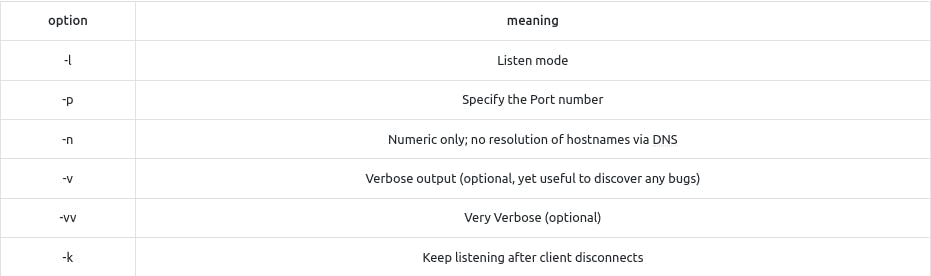
Netcat
Netcat (nc) is a versatile tool valuable to pentesters. It supports both TCP and UDP protocols, working as a client or server on chosen ports. You can use it to:
Connect to a Server: Similar to Telnet, use
nc MACHINE_IP PORTto collect server banners.Act as a Server: Set it to listen on a specific port for incoming connections.
Use TCP or UDP: Conveniently switch between these protocols for various tasks.
So, Netcat is a handy tool for connecting or hosting services over TCP or UDP, aiding in network testing and analysis.
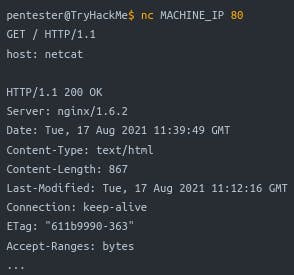
Q : Start the VM and open the AttackBox. Once the AttackBox loads, use Netcat to connect to the VM port 21. What is the version of the running server?
~ 0.17