Introduction
Burp Suite is a collection of cybersecurity tools created by PortSwigger for evaluating the security of web applications. It's widely used by security experts and ethical hackers to find and fix vulnerabilities.
Key Features:
Web Application Scanning: Automatically checks for common vulnerabilities like SQL injection and XSS.
Proxy and Intercept: Acts as a middleman to inspect and modify data between the browser and the app, revealing hidden issues.
Spidering and Mapping: Explores the app's structure by crawling through its pages and endpoints.
Manual Testing: Allows experts to manually create and modify HTTP requests to test different attack scenarios.
Vulnerability Analysis: Helps understand and rate the severity of detected vulnerabilities.
Reporting: Generates detailed reports summarizing found vulnerabilities and suggesting fixes.
Responsible Usage
Burp Suite should only be used in authorized environments, with proper consent, to assess application security responsibly.
INSTALLATION
SEE THIS LINK : https://shorturl.at/ovFHV
Download Burp Suite: Visit the PortSwigger website (https://portswigger.net/) and navigate to the "Downloads" section. Choose the appropriate version of Burp Suite based on your needs (e.g., Community Edition, Professional Edition) and your operating system (Windows, macOS, Linux)
Install Java: Burp Suite is built on Java, so you need to have Java installed on your system. Make sure you have a compatible version of Java installed. You can download Java from the official Oracle website or use OpenJDK

Install Burp Suite: Once the Burp Suite installer is downloaded, run the installer file. Follow the on-screen instructions to install Burp Suite on your system

License Activation (Professional Edition): If you're installing the Professional Edition, you'll need to activate your license. Follow the instructions provided during the installation process or after launching Burp Suite for the first time.
Configuration: After installation, you might need to configure certain settings based on your preferences and testing environment. This could include proxy settings, UI customization, and other preferences.

Start Burp Suite: Once installed and configured, you can start Burp Suite. Depending on your operating system, you can typically find it in your applications menu, launcher, or desktop shortcut.

Update Burp Suite (Optional but Recommended): Security tools like Burp Suite are frequently updated to address bugs and vulnerabilities. Periodically check the PortSwigger website for updates and newer versions, and make sure to keep your installation up to date
FOXY PROXY
INSTALLATIONS
LINK : https://youtu.be/jHGNLvSpaLs?si=vznpyOiL8EJe2veg

TOOLS
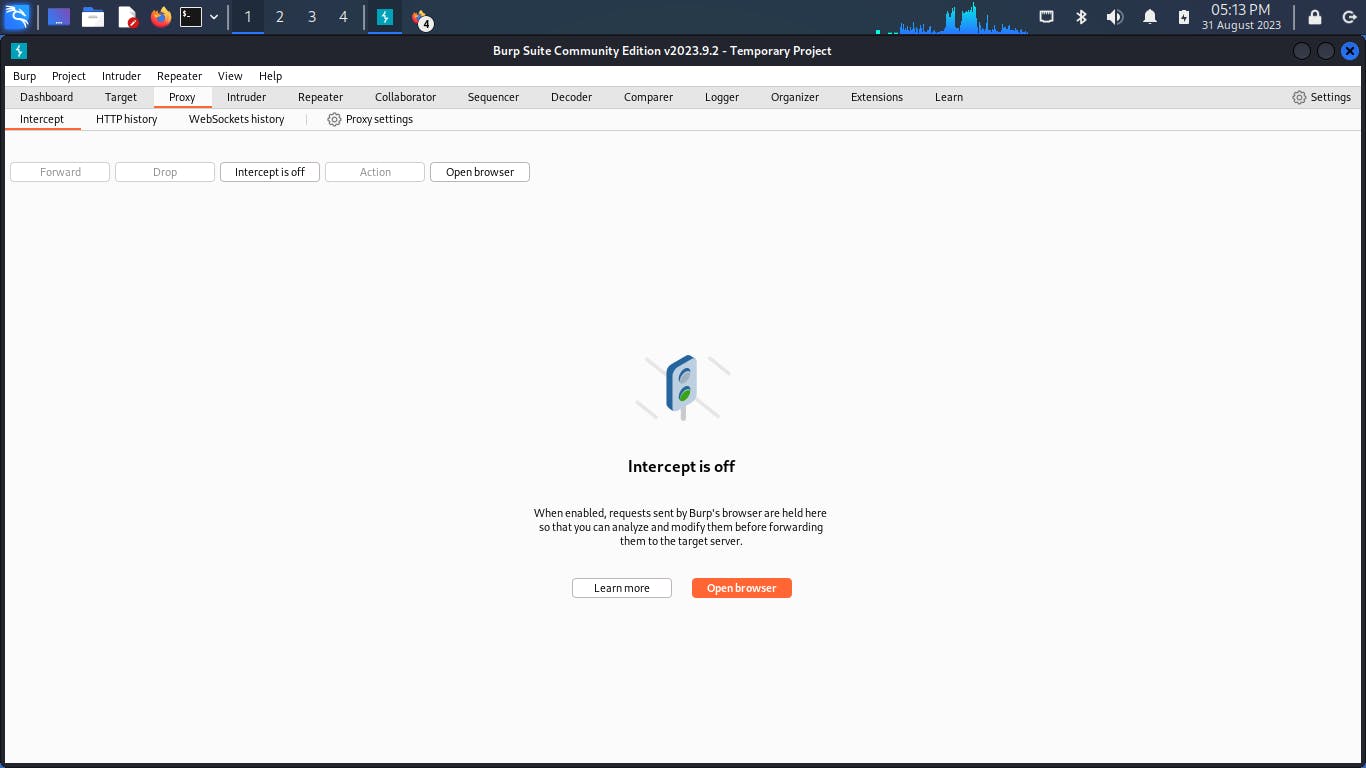
Proxy: The Proxy tool acts as an intermediary between your browser and the target web application. It lets you intercept, modify, and analyze HTTP requests and responses. This is particularly useful for manual testing and understanding how data flows between the client and server
Spider: The Spider tool automatically crawls through a web application, following links and exploring different pages and endpoints. It helps in creating a map of the application's structure.
Scanner: The Scanner tool automates the process of identifying security vulnerabilities in web applications. It performs various tests, such as looking for common vulnerabilities like SQL injection, XSS, and more.
Intruder: The Intruder tool is used for performing automated attacks on web applications. It allows you to fuzz input parameters with different values, helping to identify vulnerabilities that might not be caught by regular scanning

Repeater: The Repeater tool lets you manually modify and resend individual HTTP requests. It's useful for testing how the application responds to different inputs

Sequencer: The Sequencer tool helps in analyzing the randomness and quality of session tokens and other important values used in the application's security.
Decoder: The Decoder tool assists in encoding and decoding data in various formats, such as URL encoding, base64, and more. It's useful for understanding how data is transformed before being sent over the network.
Comparer: The Comparer tool helps you identify differences between two similar HTTP requests or responses. This can be useful when you're testing different scenarios and need to pinpoint what's changing.
Extender: The Extender tool allows you to add your own custom extensions or plugins to Burp Suite, enhancing its functionality to suit your specific needs.
Collaborator: The Collaborator tool helps in identifying blind vulnerabilities by generating unique payloads and monitoring interactions with external servers. This is useful for situations where the application doesn't directly provide feedback about successful attacks

