Passive Reconnaissance
Passive Reconnaissance involves gathering information about a target without directly engaging with it. Here are the key aspects of passive reconnaissance arranged in a short list with subpoints:
Information Gathering
Collecting data from publicly available sources.
Utilizing open-source intelligence (OSINT) techniques.
Searching for online footprints, such as social media profiles and website information.
Data Analysis
Collating and organizing gathered information.
Identifying potential vulnerabilities or weak points.
Creating a profile of the target, including its infrastructure and personnel.
Tools and Techniques
Employing tools like search engines, WHOIS lookup, and domain research.
Scanning for exposed services and ports.
Utilizing passive DNS and email analysis.
Goal
Understanding the target's digital presence.
Assessing the target's security posture.
Preparing for future active reconnaissance or attacks based on the gathered intelligence.
Legality and Ethical Considerations
Adhering to ethical hacking guidelines and laws.
Respecting privacy and consent while gathering information.
Ensuring all activities are within legal boundaries.
Risk Mitigation
Protecting one's identity and location during reconnaissance.
Using anonymity tools like VPNs or proxies.
Minimizing the traceability of data gathering activities.
Passive reconnaissance is a critical phase in cybersecurity and ethical hacking, as it provides a foundation for informed decision-making and subsequent security measures.

Q : You visit the Facebook page of the target company, hoping to get some of their employee names. What kind of reconnaissance activity is this? (A for active, P for passive)
~ P
Q : You ping the IP address of the company webserver to check if ICMP traffic is blocked. What kind of reconnaissance activity is this? (A for active, P for passive)
~ A
Q : You happen to meet the IT administrator of the target company at a party. You try to use social engineering to get more information about their systems and network infrastructure. What kind of reconnaissance activity is this? (A for active, P for passive)
~ A
Whois

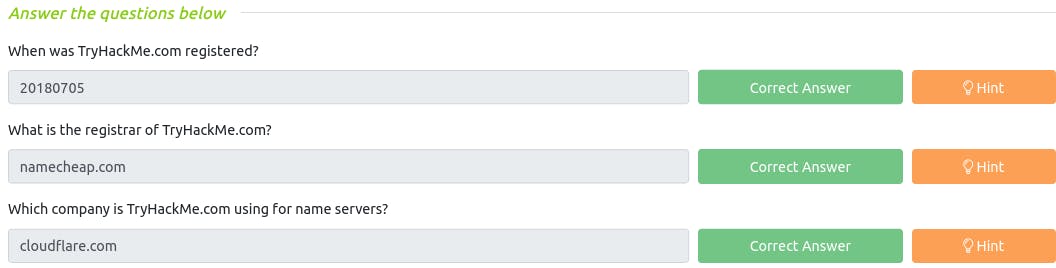
Q : When was TryHackMe.com registered?
~ 20180705
Q : What is the registrar of TryHackMe.com?
~ namecheap.com
Q : Which company is TryHackMe.com using for name servers?
~ cloudflare.com
nslookup and dig
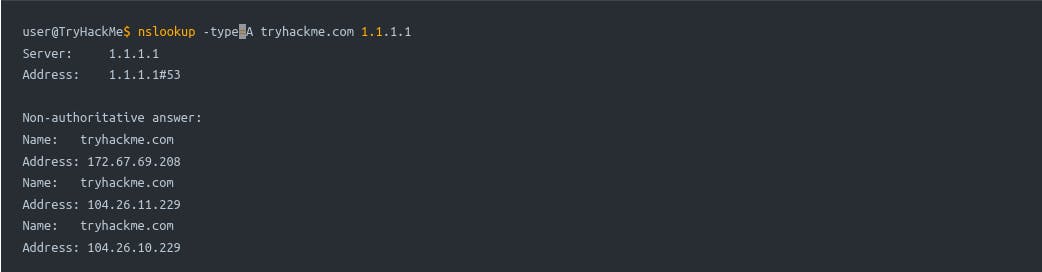
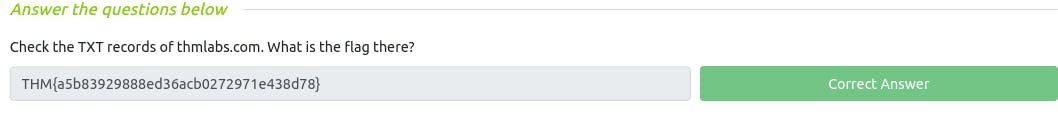
Q : Check the TXT records of thmlabs.com. What is the flag there?
~ THM{a5b83929888ed36acb0272971e438d78}
DNSDumpster

Q : Lookup tryhackme.com on DNSDumpster. What is one interesting subdomain that you would discover in addition to www and blog?
~ remote
Shodan.io

Q : According to Shodan.io, what is the 2nd country in the world in terms of the number of publicly accessible Apache servers?
~ Germany
Q : Based on Shodan.io, what is the 3rd most common port used for Apache?
~ 8080
Q : Based on Shodan.io, what is the 3rd most common port used for nginx?
~ 888