Pentesting Fundamentals | Try Hack Me |Jr Penetration Tester | By Mohit Damke
Pentesting Fundamentals | Try Hack Me |Jr Penetration Tester | By Mohit Damke

What is Penetration Testing?
A Penetration test or pentest is an ethically-driven attempt to test and analyse the security defences to protect these assets and pieces of information. A penetration test involves using the same tools, techniques, and methodologies that someone with malicious intent would use and is similar to an audit

Penetration Testing Ethics

White Hat:
White hat individuals are ethical hackers and cybersecurity professionals.
They use their skills to identify and fix security vulnerabilities, helping organizations improve their defenses.
White hats are authorized to perform security testing and penetration testing on systems, networks, and applications.
Their goal is to enhance security and protect against cyber threats.
Black Hat:
Black hat hackers are individuals who engage in malicious activities for personal gain or harm.
They exploit vulnerabilities in systems, steal sensitive data, and conduct unauthorized activities.
Their activities are illegal and unethical, often causing financial loss and damage to individuals and organizations.
They may engage in activities such as hacking, identity theft, and spreading malware.
Grey Hat:
Grey hat hackers fall in between white hat and black hat hackers.
They do not have malicious intent, but they may engage in hacking without formal authorization.
Grey hats might discover vulnerabilities and notify the affected parties, but they may also expose vulnerabilities publicly before they are fixed.
Their actions can be seen as ethically ambiguous, as they may cause harm inadvertently or by exposing sensitive information.
Rules of Engagement (ROE)

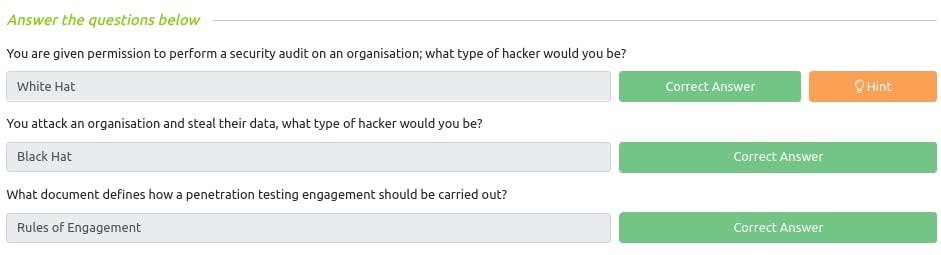
Q : You are given permission to perform a security audit on an organisation; what type of hacker would you be?
~ White Hat
Q : You attack an organisation and steal their data, what type of hacker would you be?
~ Black Hat
Q : What document defines how a penetration testing engagement should be carried out?
~ Rules of Engagement
Penetration Testing Methodologies

Q : What stage of penetration testing involves using publicly available information?
~ Information Gathering
Q : If you wanted to use a framework for pentesting telecommunications, what framework would you use? Note: We're looking for the acronym here and not the full name.
~ OSSTMM
Q : What framework focuses on the testing of web applications?
~ OWASP
Black box, White box, Grey box Penetration Testing

Black Box Penetration Testing:
Approach: Testers have no prior knowledge of the system being tested.
Simulation: Mimics an attacker with no internal information.
Benefits: Tests real-world vulnerabilities, simulates external threats.
Limitations: May miss internal vulnerabilities, can be time-consuming.
White Box Penetration Testing:
Approach: Testers have full knowledge of the system's internals.
Simulation: Simulates attacks with detailed information.
Benefits: Efficient for pinpointing vulnerabilities, thorough analysis.
Limitations: Might miss real-world attack scenarios, lacks external perspective.
Grey Box Penetration Testing:
Approach: Testers have partial knowledge of the system, often limited to high-level details.
Simulation: Combines external threat simulation with some internal knowledge.
Benefits: Balances real-world attacks and insider insights.
Limitations: May not fully capture complex attack vectors

Q : You are asked to test an application but are not given access to its source code - what testing process is this?
~ Black Box
Q : You are asked to test a website, and you are given access to the source code - what testing process is this?
~ White Box
Practical: ACME Penetration Test

Q : Complete the penetration test engagement against ACME's infrastructure.
~ THM{PENTEST_COMPLETE}

