Introduction
Key Points:
1. Understanding Vulnerabilities:
- What vulnerabilities are and why they matter.
2. Significance of Learning About Vulnerabilities:
- Why gaining knowledge about vulnerabilities is essential in the field of cybersecurity.
3. Vulnerability Ratings Demystified:
- Unpacking how vulnerabilities are rated and the criteria used for assessment.
4. Resources for Vulnerability Research:
- Valuable databases and tools to aid in comprehensive vulnerability research.
5. Real-world Application:
- A practical showcase of vulnerability research in action, featuring an engagement by ACKme.
By the end of this article, you'll have a solid grasp of vulnerabilities, their importance, and the resources at your disposal for effective vulnerability research, ultimately enhancing your penetration testing skills.
Introduction to Vulnerabilities

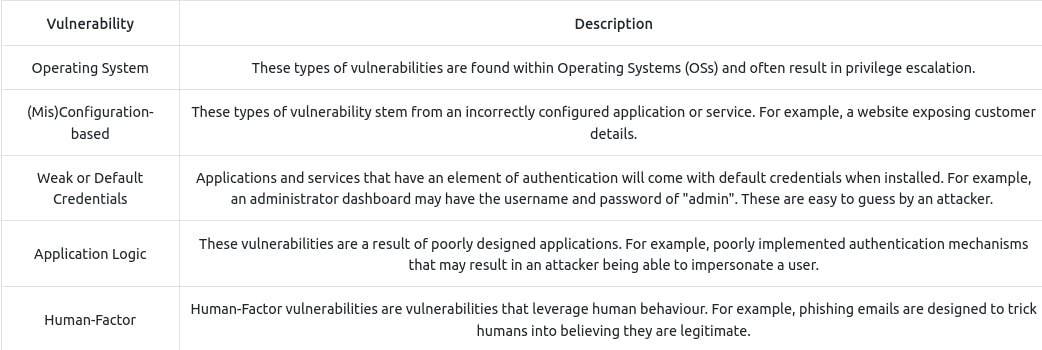
Q : An attacker has been able to upgrade the permissions of their system account from "user" to "administrator". What type of vulnerability is this?
~ Operating System
Q : You manage to bypass a login panel using cookies to authenticate. What type of vulnerability is this?
~ Application Logic
Scoring Vulnerabilities (CVSS & VPR)
The Common Vulnerability Scoring System (CVSS) is a widely adopted framework for assessing and scoring vulnerabilities. Introduced in 2005, it has evolved through three major iterations, with CVSSv3.1 as the current version (with version 4.0 in draft). CVSS assigns a score to vulnerabilities based on various factors, including:
1. Ease of Exploitation:
- This factor evaluates how straightforward it is for a malicious actor to exploit the vulnerability. Vulnerabilities that are easier to exploit typically receive higher scores.
2. Existence of Exploits:
- The presence of known exploits in the wild can significantly impact a vulnerability's score. Vulnerabilities with readily available exploits tend to receive higher scores.
3. Impact on the CIA Triad:
CVSS considers how a vulnerability affects the three core principles of the CIA triad: Confidentiality, Integrity, and Availability. A vulnerability's impact on these principles plays a crucial role in determining its score.
Confidentiality: Does the vulnerability jeopardize the confidentiality of data or information? Higher impact on confidentiality leads to a higher score.
Integrity: How does the vulnerability affect the integrity of data or systems? Higher impact on integrity results in a higher score.
Availability: Does the vulnerability impact the availability of resources or services? Higher impact on availability leads to a higher score.
CVSS provides a standardized way to assess vulnerabilities, enabling organizations to prioritize and address them based on their severity. This scoring system aids cybersecurity professionals in making informed decisions about vulnerability mitigation and resource allocation
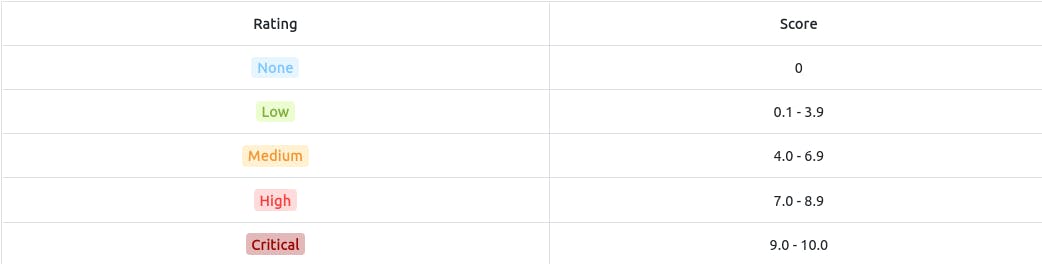

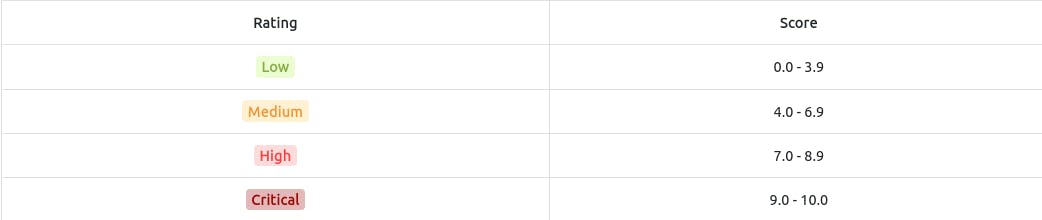
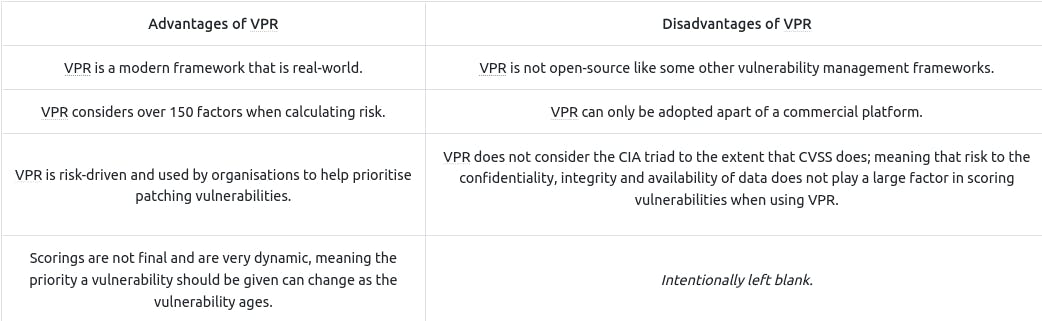
VPR :
Vulnerability Priority Rating (VPR) is a holistic cybersecurity metric that factors in business impact, ease of exploitation, exploit availability, and organizational relevance to prioritize vulnerability responses effectively
Q : What year was the first iteration of CVSS published?
~ 2005
Q : If you wanted to assess vulnerability based on the risk it poses to an organisation, what framework would you use?
~ VPR
Q : If you wanted to use a framework that was free and open-source, what framework would that be?
~ CVSS
Vulnerability Databases
NVD – National Vulnerability Database
The National Vulnerability Database (NVD) serves as a comprehensive repository of publicly categorized vulnerabilities in the world of cybersecurity. These vulnerabilities are organized and tracked under the "Common Vulnerabilities and Exposures" (CVE) system, denoted in the format CVE-YEAR-IDNUMBER. For instance, the infamous WannaCry malware leveraged the CVE-2017-0144
Exploit-DB
Exploit-DB is a resource that we, as hackers, will find much more helpful during an assessment. Exploit-DB retains exploits for software and applications stored under the name, author and version of the software or application
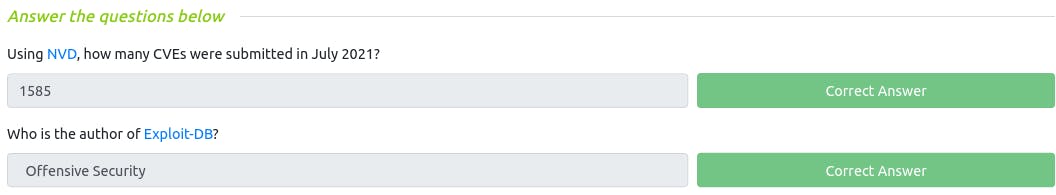
Q : Using NVD, how many CVEs were submitted in July 2021?
~ 1585
Q : Who is the author of Exploit-DB?
~ Offensive Security
An Example of Finding a Vulnerability
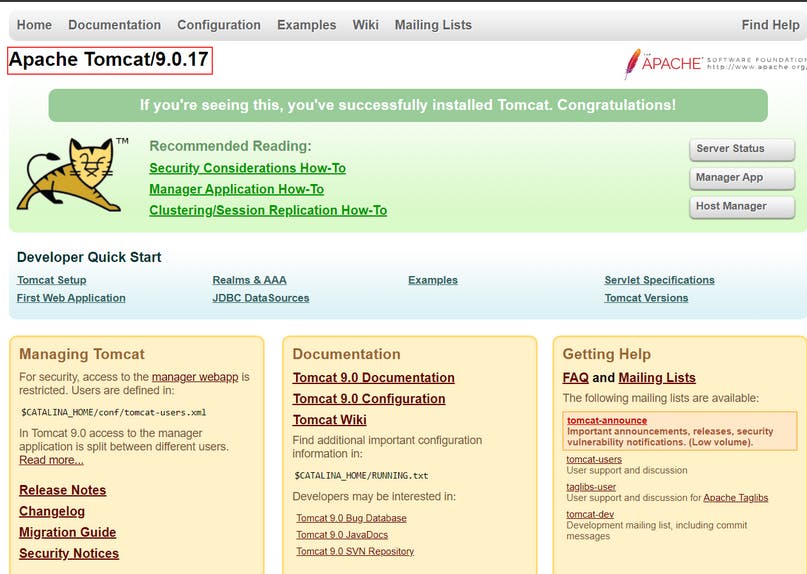
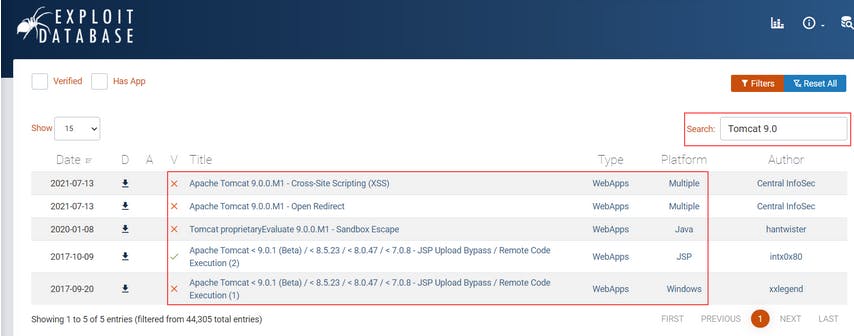
Q : What type of vulnerability did we use to find the name and version of the application in this example?
~ Version Disclosure
Showcase: Exploiting Ackme's Application
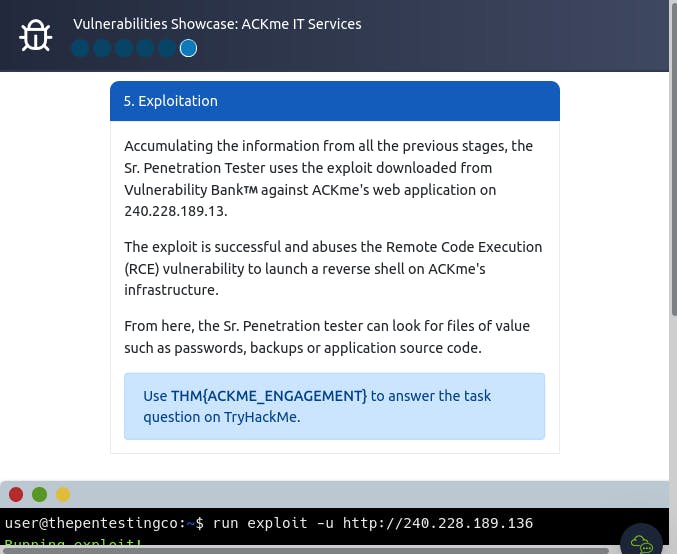
Q : Follow along with the showcase of exploiting ACKme's application to the end to retrieve a flag. What is this flag?
~ THM{ACKME_ENGAGEMENT}